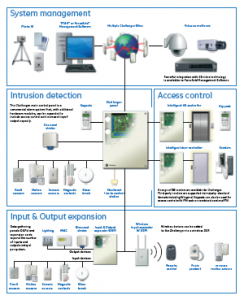
Access control system operation When a credential is presented to a reader, the reader sends the credential’s information to a control panel. The control panel compares the credential’s number to an access control list, grants or denies the presented request and sends a transaction log to a database.
GE Security Challenger Integrated Security Platform
Access control
 A Population count.
A Population count.
Prevents access when a pre-determined limit of users is reached. Can trigger an output such as “Car Park Full” sign.
B Out of hours access.
Increase security after business hours by requiring both an access card and a PIN code.
C 24-hour access.
Manager has complete access to premises at all times.
D Fingerprint scanning.
Optional biometric reader can be used to provide higher-security access control.
E Anti-passback support.
Challenger can prevent entry (hard anti-passback) or allow entry whilst reporting the event (soft anti-passback).
F Dual card entry.
Requires two different users to present their access cards in sequence to unlock high security areas.
G Interlocking doors.
Requires one of the doors to be closed before the other can be opened.
H Restricted access hours.
Contract workers’ access can be limited to normal working hours.
I Restricted access rights.
Workers’ access can be limited to specific floors and doors.
System management
 A Remote system access.
A Remote system access.
Authorised command and control of the Challenger system from PC software with graphical map display.
B Administration support.
HR/payroll can export employee time and attendance information from the system.
C Visitor management.
Receptionist can issue temporary access cards with programmable expiry time and date.
For more information, please contact us on 0488 033 022 or via Email Leact.Lee@gmail.com
